- Click the Download button in the pickup wizard to download your certificate files. Clicking the download button will produce a zip file that includes your Server Certificate, the Entrust Intermediate certificate and the Entrust Root certificate. Extract the files from the zip file.
- For instance, if I select Root Certificates, I then see several options, each with several files, and none of them are a PEM file: Entrust.net Secure Server Certification Authority; Entrust.net Certification Authority (2048) Entrust Root Certification Authority; Entrust Root Certification Authority - G2; Entrust Root Certification Authority - EC1.
- Download Entrust Root Certification Authority G2 On Macbook Pro
- Entrust Root Ca
- Download Entrust Root Certification Authority G2 On Mac Os
Download DigiCert Root and Intermediate Certificate. DigiCert Root Certificates are widely trusted and are used for issuing SSL Certificates to DigiCert customers—including educational and financial institutions as well as government entities worldwide. If you are looking for DigiCert community root and intermediate certificates, see DigiCert Community Root and Authority Certificates.
Certificate Chains
Most digital certificates problems are caused by broken certificate chains.
A certificate chain is a string of certificates from the one you are using (e.g., your certificate) to a certificate that is trusted by your computer. The first link of the chain is a self-signed certificate that a Root Certificate Authority (CA) issues to itself. The next link of the chain is a certificate that the Root CA issues to a Subordinate CA. The last link of the chain is an end-entity certificate that a Subordinate CA issued to you, a webserver, or some other person or device. A certificate chain is broken if your computer does not trust the Root CA or cannot find the certificates that link the end-entity to the trusted root.
The following certificate chains are used at NIH as part of the HHS PKI:- Entrust FPKI Certificate Chain
Used to trust smart cards and some internal NIH webservers. - Entrust Public TLS certificate chain
Used to trust some public facing webservers and the NIH VPN. - Older Entrust Public TLS certificate chain
Used to trust some public facing webservers and the NIH VPN. - HHS Device Certificate Chain
Used by your desktop to support smart card login.
NIH DPKI Certificate Chain and CRLs
Please refer to the guides below before downloading and installing these certificates.
NIH Device PKI Certificate Chain/pwgenerator-163.html.
This certificate chain will replace the current HHS Device Certificate chain based on the SHA-1 algorithim which will soon be deprecated. It will be the trust path used by NIH desktops, servers and other devices to trust NIH Domain Controllers certificates during smart card logon process. The NIH DPKI certificates must be installed in the certificate stores of all Windows, Macs, Unix/Linux, and other devices that will be participating in PIV card authentication with NIH Domain Controllers.
NIH-DPKI-ROOT-1A.cer (expires 9/17/2045)
NIH DPKI Certificate Revocation List (CRL)
NIH DPKI CRLs can be downloaded from this link: http://NIHDPKICRL.NIH.GOV/CertData
Note: NIH DPKI CRLs should be automatically downloaded to your Windows and Mac computer and is only needed if your computer cannot access:
- Active Directory LDAP CRL location
HHS PKI Certificate Chains and CRLs
Please refer to the guides below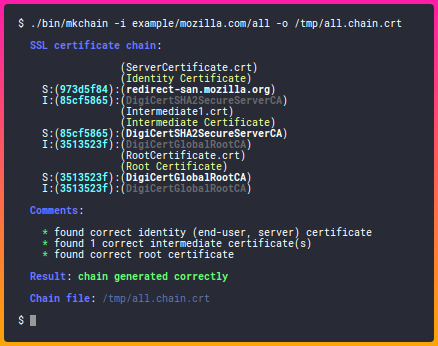
 before downloading and installing these certificates.
before downloading and installing these certificates. HHS Entrust FPKI Certificate Chain
This certificate chain is the trust path used by HHS smart card certificates (issued since 9152013) and HHS Internal Common Policy TLS certificates issued by Entrust. See below for instructions on installing this chain on a Macintosh computer.
Federal Common Policy CA(expires 12/1/2030)
Entrust Managed SErvices Root CA.cer(expires 7/30/2025)
HHS-FPKI-Intermediate-Rollover-2017.cer (expires 7/20/2025)
Your PIV Certificate
HHS Public Entrust TLS Certificate Chain
This is the most recent certificate chain trust path used by HHS External Public Trust TLS certificates issued by Entrust.
Entrust Root Certification Authority -G2 (expires 12/02/2030)
Entrust Certification Authority -L1K (expires 10/23/2024)
NIH Webserver
HHS Public Entrust TLS Certificate Chain
This is an older, but still used, certificate chain trust path used by HHS External Public Trust TLS certificates issued by Entrust.
Entrust.net Certification Authority (2048) (expires 7/24/2029)
Entrust Certification Authority -L1C (expires 11/11/2021)
NIH Webserver
The following guides will help you diagnose and fix certificate chain problems:
You may need system administrative privileges to install root certificates. If you do not have system administrative privileges, please contact the NIH IT Service Desk to have these certificates installed on your computer.
Download Entrust Root Certification Authority G2 On Macbook Pro
Information and Assistance
Entrust Root Ca
For additional information, search the NIH IT Knowledge Base for tutorials, instruction sheets and user guides or refer to the appropriate How-To Guide.
Download Entrust Root Certification Authority G2 On Mac Os
For questions or user support, please contact the NIH IT Service Desk.