- Hack Android Lewat Mac Address Windows 10
- Hack Android Lewat Mac Address Windows 7
- Hack Hp Lewat Mac Address Di Android
- Hack Wifi Lewat Mac Address Android
- Hack Wifi Lewat Mac Address Di Android
Jika komputer kamu terhubung dengan sebuah jaringan atau internet, maka komputer kamu akan memiliki Internet Protocol address (IP address) di komputer kamu. Saat ini komputer banyak yang menggunakan Internet Protocol Versi 4 (IPv4), angka-angka ini ada empat kelompok yang dipisahkan dengan periode, sebagai contoh 172.205.77.65. IP Address merupakan elemen penting dalam.
Hack WhatsApp Account with Mac Address Spoofing : Hi Guys, As we all know Whatsapp is a most popular messaging app on the social media platform. Billions of people are using this application all over the world. Almost every people is using WhatsApp account. In WhatsApp, you can share your photos, videos, recording, location and more thing easily. Everyone uses this WhatsApp message on their phone no matter which os you use. You can easily use Whatsapp in Android, Iphone, Blackberry, Windows smartphones.
So Guys Today I have a very interesting and useful topic for you that is hack WhatsApp account with mac address. most of you are search on google for WhatsApp hacking. Our previous post lots of people text us for making the article on WhatsApp account hacking fully so after reading your messages we make this article for you. As we already tell you about hacking and most of the people say that hacking is not piece of cake. Yes, they all are right but you are with us and we always try to give you best hacking tricks in a legal way. Some people use phishing page for hacking someone id or password and other detail but now the time everyone knows about that type of tricks but today talk about WhatsApp and you can’t hack Whatsapp by phishing page.
Here is the new article on Whatsapp tips and tricks. As we discuss above that today we tell you how to hack WhatsApp account with MAC address. Our previous trick is not for working all the time so here is the new trick which works every time everywhere. Previous WhatsApp trick is working only sometimes when the victim will be connected with our network but this WhatsApp hacking trick totally different than the previous one. So here we give you the best Whatsapp hacking trick which you can use any time or anywhere no matter victim’s network is same as yours. you can easily use or check victims WhatsApp account after reading this article.
Steps to Hack Whatsapp account with Mac address :
By following below steps you can easily hack and use your friends or some others WhatsApp account. There is three popular method for hacking Whatsapp account. We already discuss one method in our previous post and second method we will discuss in this article, For the third method you need to pay some money so we can’t discuss the third method in this article. We discuss only second method because of it free and workable, so let’s start.
1. Whatsapp Uninstall
Firstly go to play store, search Whatsapp messenger and uninstall Whatsapp from your device. Make sure you that your Whatsapp account will completely uninstall from your android device.
Note – If you are worried about your Whatsapp account so doesn’t worry about it, you can easily reinstall your Whatsapp account whenever you want.
2 . Get victim’s phone
Get the victim’s android phone which you want to access. You need the victim;s phone for few mints for the hacking process.
3. Find MAC (Media Acess Control) address from the victim’s phone
We don’t know which OS platform is victim use. So below we give you all smartphone platform, with these you will easily find MAC Address from victim;s phone.
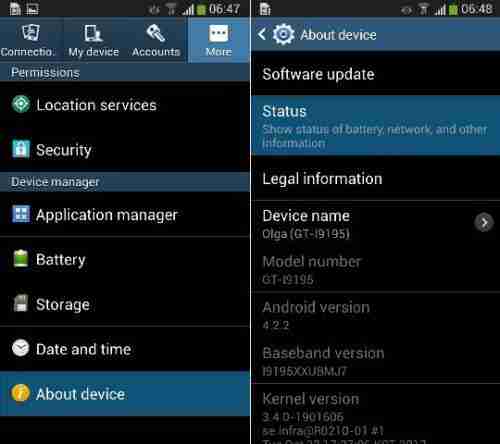
Android : Go to the setting > About phone > wifi MAC address
Iphone : Go to Setting > General > About > MAC Address.
Window Phone : Go to Setting > About > More Info > MAC address
Blackberry : Option > Go to Device >Device and Status Info > WLAN MAC
4 . Save Victim’s MAC address
After finding a MAC address, you have to save MAC address on the paper or where you want. Make sure you save right MAC address.
5. Find MAC Address of your own device
Get your mac address of your smartphone and save it for future when you want to access your own Whatsapp account.
6. Spoofing your mac address
Now you need to spoofing your Mac address. Spoofing is allowed your mobile to look like as victim’s phone. After spoofing you will access Whatsapp account but not your’s. You will access victim’s Whatsapp account.
7. Install Spoofing app
By spoofing app, you can easily change your MAC address. After installed spoofing app you have to change your MAC address with victim phone’s MAC address.

Spoofing app for android user
BusyBox, Terminal Emulator
Spoofing app for iPhone user
Mac Daddy X, Wifi Spoof
8. Re-install Whatsapp Messenger on your device
After Spoofing MAC address and Installing Whatsapp Messenger on your device, you can easily access victim’s Whatsapp account just follow a few more steps.
- Open Whatsapp messenger and enter victim’s mobile number.
- Now take victim’s phone for few second because after entered victim’s number, you have to get Whatsapp confirmation code from victim’s phone.
- After getting code fill it into Whatsapp on your phone and delete confirmation message from victim;s phone.
Now you have successfully hacked victim’s Whatsapp account. I hope, you have enjoyed this article. In case you’ll face any problem regarding this article so don;t be shy feel free and comment on below comment box. We will solve your problem as soon as possible. For more updates of tip and tricks like us on Facebook, follow us on Instagram and twitter. We also have a youtube channel so subscribe us for more hacking videos and tricks things.
I am also facing the same issue, WhatsApp stopped working on the victim device after I activated it on my device. And when I changed the Mac address of my device back to the original, it displayed the message ‘your phone number is no longer registered on this phone’ on the victims phone.
by hash3liZer . 12 April 2018
The usage statistics of the android platform has been significantly increased over the last decade and it's rather crucial to discuss how well it have passed the stages of security in terms of trojans and the most competing viruses of today.
Just as the windows platform can be compromised if necessary precautions are not taken, the same could be said for the android. Over the years various practices have been taken into account to circumvent these security policies of android platform and metasploit being one of those.
Metasploit
An exceptional powerful tool named metasploit is basically a tool written in ruby and is quite handy at being used as a secondary command line interface. It provide access to diverse modules, each with an intended task to perform, and are further categorized into sub-modules.
Metasploit is famous among the researchers because of it's handy interface and the large database of exploits that it offers.
Everyday or week, when a new severe vulnerability gets discovered, the developers of metasploit would publish it publicly on the ExploitDB platform. Read more about gaining access to multiple platforms with shellpop:
Setup a remote Backdoor on Windows/Linux for system access.
Anti-Virus Softwares and the Firewalls are very well acquainted with metasploit payload signatures and how it obfuscates the payload which is to gain the backdoor access.
So, the AV detects the virus and move it away instead of letting it execute. Hence, being a strong guarding agent in the way of metasploit.
Let's see how we can gain access to an android smartphone with metasploit:
Virtual Dj For Chrome Book 15 Newest Virtual free download - Virtual CD, Virtual WiFi Router, Virtual Audio Cable, and many more programs. VirtualDJ has been around for more than 20 years, and has been downloaded by more than 126,000,000 people, making VirtualDJ the most downloaded DJ software on earth! It is used daily by millions of professional DJs all around the world. Filled with all the latest technology, VirtualDJ will help you take your DJing skills to the next level. Virtual dj download for chromebook.
STEP 1
Preparing Metasploit
Open the console (terminal). Check the weekly updates and make changes to metasploit if necessary or if any new modules are detected. Doing so will keep you informed of newly added modules and exploits.
After that, start postgresql database service. Metasploit uses postgresql as the storage database. This will enable us to quickly navigate and search through metasploit modules, preventing the slow search issue that wastes time while systematizing the output.
Enabling the postgresql will start it everytime the system boots. Now, there's no need to perform this step, next time, metasploit is going to flash.
Type msfconsole in terminal and press [Enter]. It will take a few seconds to bring the interface up to its fully functional state.
STEP 2
Choose the exploit
Search for an appropriate exploit for target OS using search command. Our target is an android smartphone. So, the query for an Android could be like:
It will list the exploits available for android platform. You can get help on metasploit commands by typing help followed by a space with command name such as help search. It will print the manual for search command. Here's the output for android exploit search:
From the given list of exploits as shown in the image, we will use the generic exploit as highlighted. Now, to use the exploit, enter this command:
There is a set of payloads given for every single exploit. These payloads are actually the exploit modules that provides a backbone environment for transferring and executing commands on target window. Different payloads are used according to the given scenario and by guessing how much working space of target is required. Well, to show the payloads given for an exploit. Type in:
From the given set of payloads, we will use android/meterpreter/reverse_tcp. It's a great versatile payload to get started with. It will bring us a meterpreter session if payload executes unspotted. This meterpreter payload presents a handful list of directives which are useful enough to wholly compromise the target system.
Hack Android Lewat Mac Address Windows 10
At this point we need to know the basic difference between reverse and bind payloads. Bind payload will let you open a connection on the target system while the reverse payload would open a listening connection on the target machine, making it the host.
For the quick info, bind payloads are more useful when the target is a server or a device which is directly connected to internet and have a static IP. Reverse payloads are rather more adopted because of the nature of it's working.
Because most of the computers are behind NATon the internet, it's most likely that the bind payload is not going to work in this situation. Set the payload :
STEP 3
Set Options
Attain the information of exploit using info command. This is the key step to get an idea, how actually the exploit works. It will give you the background information like what could be the possible targets and what the core of vulnerability is.
At this point, we know the working of exploit. Now, we have to setup the options for our exploit which are LHOST for local address of attacker and LPORT for the local port to use. To find local IP address type.
So, my local IP is 192.168.1.10. Set LHOST and LPORT
Lexmark printer app for mac. Make sure that both of the paramters are correctly modified.
STEP 4
Run the Exploit
Run the exploit as a job. The exploit will execute in the background and will notify you whenever the payload executes on the target system. Afterward, we will use sessions command to launch (target) session.
STEP 5
IP Forwarding
Find the Gateway IP of your Network and navigate to that IP through a web browser and login. Type:
Now, open a web browser and login to Router administrative Page.
After successful login, enable the port 777 so that firewall allows the client and attacker machines to forward and receive traffic. You probably don't know how to forward a port on your router. For doing so, go to PortForward.com, search for your router company and model and follow the instructions for your router.
STEP 6
Generate (Infected) Application
For generating the infected (payload) application with extension .apk, we will use msfvenom, native payload generator of Metasploit framework. Open a new console (terminal) and generate a Simple Payload Application for android.
PARAMETER BREAKDOWN
- -p: payload to use
- --platform: Target Platform
- -o: Path to place the infected file
- LHOST: Public IP of attacker (local) Machine
- LPORT: Public Port of attacker (local) Machine
STEP 7
Own the target
Now, as soon the spawned apk file will be installed on an android Operating System (target). Metasploit terminal which we have left open will bring us a live target session. List the available sessions:
Now, to interact with a session. Just type in the session identifier (ID) after the sessions directive. It will take you to the meterpreter shell.
Meterpreter session will be launched. Type help command. It will list a handful of commands from getting system info to starting live Chat.
Hack Android Lewat Mac Address Windows 7
Ignore meterpreter > . Its just there to indicate that its a meteterpreter session.
Hack Hp Lewat Mac Address Di Android
Lets try the shell command. It will bring us the terminal or cmd (if windows) of target system. Try to execute a command.
Hack Wifi Lewat Mac Address Android
Conclusion
Hack Wifi Lewat Mac Address Di Android
Android is the most widely adopted Operating System, making it the most famous platform even decisivly leaving windows behind and on the verge of security policies. Just like other platforms, android can be compromised with a few considerations in mind and metasploit can help us being one of those. However, one moust note that the security in terms of android as compared to windows is usually considered more secure and liable to rely on.